Introduction to Microsoft Defender XDR
Categories: Cybersecurity
Tags: Cloud Computing
This documentation is based on Microsoft's SC-200: Mitigate threats using Microsoft Defender XDR Learning Path (link). It is a collection of notes I have written that is freely available to read.
Mitigate threats using Microsoft XDR
Vocab
Policy: A set of rules or configurations that manage how devices and apps behave in your organization
Triage: It is a response approach to a cyber incident.
Security Information and Event Management (SIEM): A software system that collects, analyzes and correlates security data/logs. It is crucial for forensics.
Security Orchestration, Automation and Response (SOAR): A system software that offers automation capabilites and enable executions. It relies on data from SIEM or any SIEM-like software to streamline the process.
Extended Detection and Response (XDR): A recent software system that integrates multiple security features as one. It is the mixed child of SIEM and SOAR with complete visibility of the IT infrastructure.
Microsoft XDR (Extended Detection and Response) is a unified security tool suite in Microsoft Azure. It is Microsoft's XDR implementation for Microsoft Azure.
Microsoft Sentinel: It is both a SIEM and SOAR solution (mostly SIEM) that gathers intelligent security analytics and automates policies across the entire organization (i.e. all users, devices, applications, infrastructure etc.).
Microsoft XDR
Inside Microsoft Azure, we have Microsoft XDR. It is a SOAR solution that forms the basis of Azure's security with various tools as illustrated below:
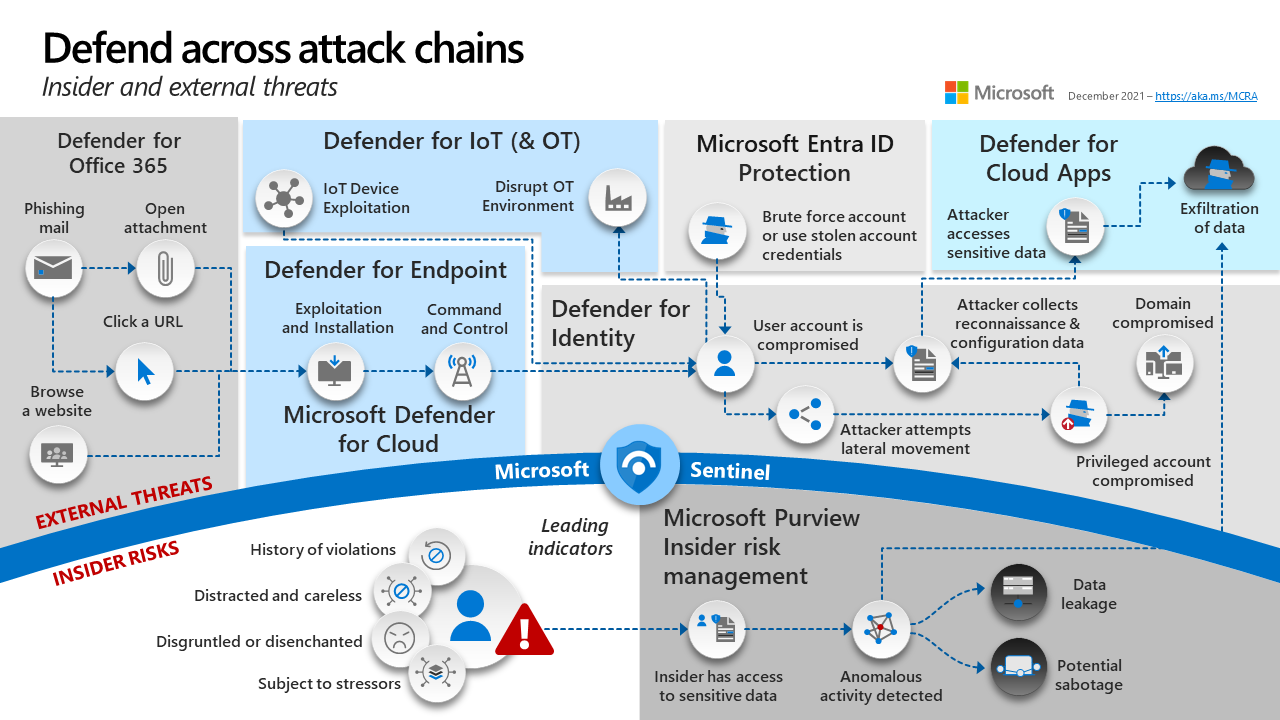
Microsoft XDR integrates tools like:
-
Microsoft Defender for Endpoint (MDE)
- Purpose: Endpoint protection
- Detects: Malware, ransomware, and advanced persistent threats on devices
-
Microsoft Defender for Office 365 (MDO)
- Purpose: Email and collaboration security
- Detects: Phishing emails, malicious attachments, and unsafe links
-
Microsoft Defender for Identity (MDI)
- Purpose: Identity-based threat detection
- Detects: Active Directory domain compromises, lateral movement (unauthorized access of an entry point to the rest of the network), and credential theft
-
Microsoft Defender for Cloud Apps
- Purpose: SaaS app security (i.e. here's a Salesforce example
- Detects: Shadow IT, app-based threats, data leakage, and risky user behaviors
Below Microsoft Sentinel, we see the different types of observable data to analyze and Microsoft Purview Insider Risk Management to manage risks alerted of user actions and data misuse.
Microsoft XDR's Response Use Cases
If the victim receives a malicious file on its inbox or through USB not protected by MDO, MDE immediately notifies the security team and will flag the device as high risk. MDE will either remediate this threat automatically, with pre-approved automatated actions, or after manual investigations.
The progression for remediation is as follows:
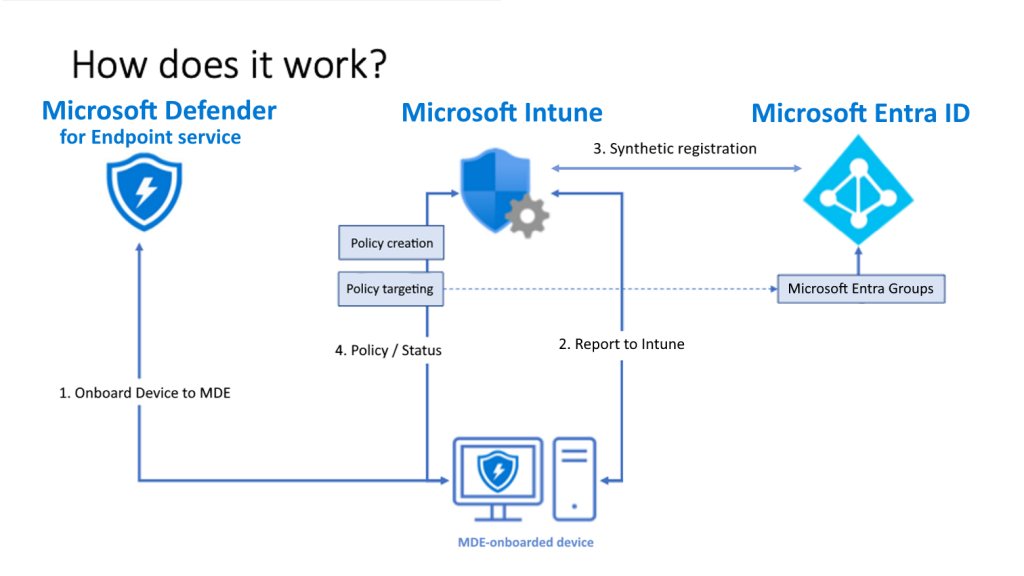
- MDE asseses the device's security risk level.
- MDE sends the device risk level to Intune. Intune will evaluate the risk level against its compliance policies.
- If the device is noncompliant, Entra ID will create Conditional Access (policy restrictions) to enforce access restrictions to corporate resources.
Note:
- Microsoft Entra ID is the new name for Azure Active Directory (or Azure AD) since 2023.
- Think of Conditional Access as the gatekeeper, Intune as the policy enforcer, and MDE as the security scanner.
- "Policy" is just another word for "rules".
Once the threat has been cleaned up, MDE will trigger Intune again to update the device's compliance policies on Entra ID. This will remove any policy restrictions on the device.
Security Operations Model
While the assignment of responsibilities to individual people and teams vary based on organization size and other factors, security operations are composed of several distinct events:
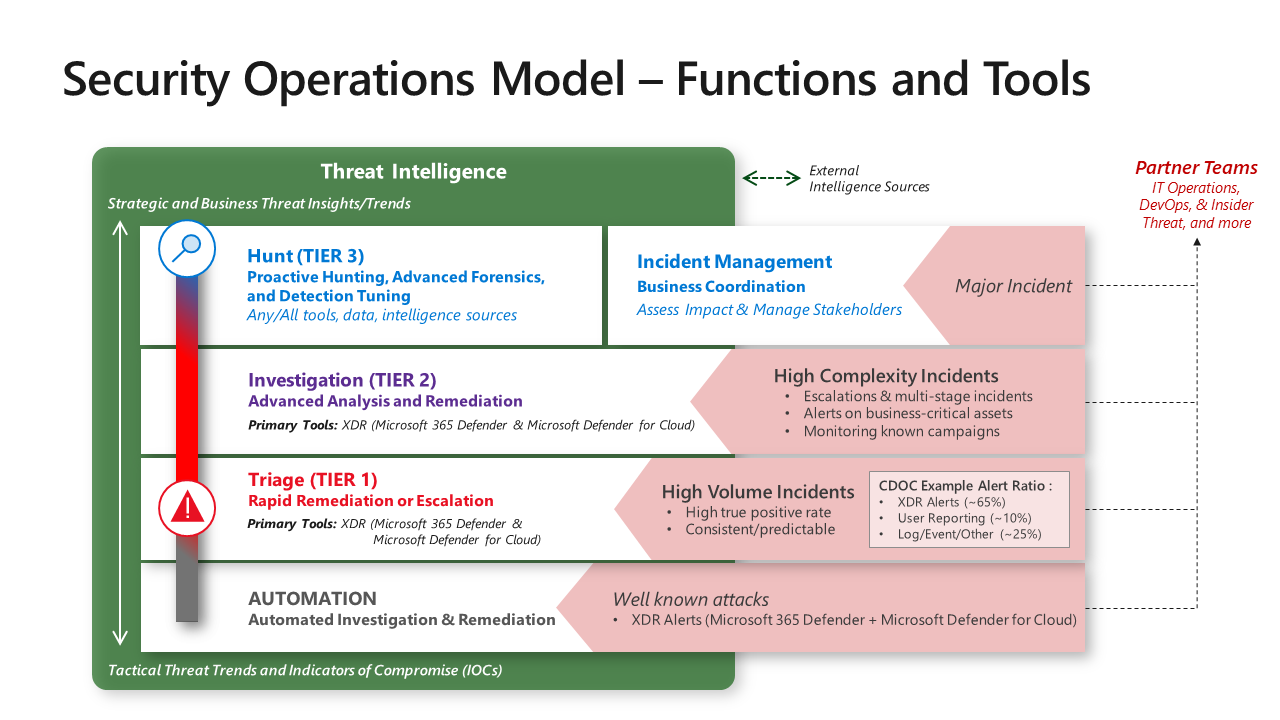
- Automation: Known common incidents that are resolved automatically.
- Triage 1: It is the first human touchpoint. It requires quick human judgement that involves pre-approved automated remediation workflows or identify anything to prevent any escalation for triage 2.
- Triage 2: Serves as the escalation point of triage 1 and indicates a more sophisticated attack. It will trigger behavioral alerts, business-critical special case alerts, and monitoring for ongoing attack campaigns.
- Triage 3: Requires a multi-disciplinary team to troubleshoot and identify attackers that slipped through detectors and handle major business-impacting events.
Microsoft Graph Data
Imagine you want to access Outlook API, Microsoft 365 API, OneDrive API, Teams API, Excel API etc. without having to learn all APIs separately. This is where Microsoft Graph gets useful:
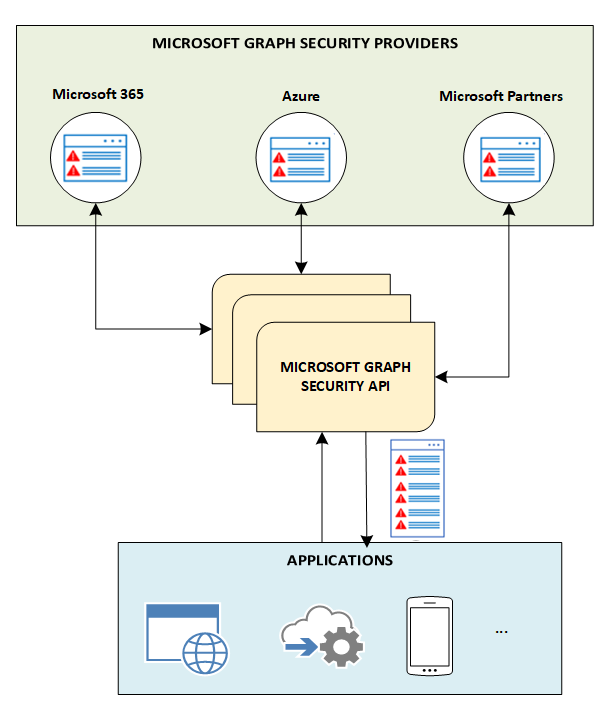
It abstracts the complexity of individual service APIs by providing a unified, consistent, and secure way to interact with Microsoft cloud data.
It offers a single endpoint to access and build apps that support:
- Microsoft 365 core services: Bookings, Calendar, Delve, Excel, Microsoft Purview eDiscovery, Microsoft Search, OneDrive, OneNote, Outlook/Exchange, People (Outlook contacts), Planner, SharePoint, Teams, To Do, Viva Insights
- Enterprise Mobility + Security services: Advanced Threat Analytics, Advanced Threat Protection, Microsoft Entra ID, Identity Manager, and Intune
- Windows services: activities, devices, notifications, Universal Print
- Dynamics 365 Business Central services
Mitigating with Microsoft Defender
Where do we see that?
Microsoft Defender Portal
Microsoft Defender Portal is a specialized workspace designed to meet the needs of security teams.
On it, admins can see alerts that affect their network. They will understand what they mean, and gather evidence associated with such incidents.
The portal lets you have access to the following features:
-
Microsoft Defender for Office 365: Secure email and Office 365 operations with a set of prevention, detection, investigation and hunting features.
-
Microsoft Defender for Endpoint: Prevents enterprise devices from malware by offering protection, post-breach detection, automated investigation.
-
Microsoft Defender XDR: It is the implementation of XDR by Microsoft. It uses the Microsoft 365 security portfolio to automatically analyze threat data across domains, and build a picture of an attack on a single dashboard.
-
Microsoft Defender for Cloud Apps: Is a comprehensive cross-SaaS and PaaS solution bringing deep visibility, strong data controls, and enhanced threat protection to your cloud apps.
-
Microsoft Defender for Identity: Is a cloud-based security solution that uses your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
-
Microsoft Defender Vulnerability Management: Delivers continuous asset visibility, intelligent risk-based assessments, and built-in remediation tools to help your security and IT teams prioritize and address critical vulnerabilities and misconfigurations across your organization.
-
Microsoft Defender for IoT: Operational Technology (OT) involves the specialized hardware and software used to monitor and control physical processes in critical sectors such as manufacturing, utilities, pharmaceuticals, and more. Microsoft Defender for IoT, available within the Microsoft Defender portal, is designed to secure OT environments.
-
Microsoft Sentinel: Integrate Microsoft Defender XDR with Microsoft Sentinel to stream all Defender XDR incidents and advanced hunting events into Microsoft Sentinel and keep the incidents and events synchronized between the Azure and Microsoft Defender portals.
Incidents
Where can we find them?
Incidents and Alerts --> Incidents
Incident: A collection of connected alerts that make up the story of an attack.
Microsoft XDR will automatically aggregate malicious and suspicious software found on different devices, users, and mailbox entities in the network. This is done through Artificial Intelligence.
Under the "incidents" page, you will see that Microsoft XDR by default organizes incidents by order of severity in the last 30 days. You can sort through them by filters or prioritize while creating an informed cybersecurity response decision.
Here are the filters available to order or prioritize below:
| Filter | Description |
|---|---|
| Status | Limit the list of incidents shown based on their status (active or resolved). |
| Severity | Indicates the potential impact an incident can have on assets; higher severity requires more immediate attention. |
| Incident assignment | Show only incidents assigned to you or those handled by automation. |
| Multiple service source | Choose No (default) or Yes to only see incidents with multiple service sources. |
| Service sources | Filter to only see incidents from different Microsoft security products (Defender for Endpoint, Cloud App Security, Defender for Identity, Defender for Office 365). |
| Tags | Filter based on assigned tags. Available tags appear once you select the tag name field. |
| Multiple category | View only incidents mapped to multiple categories, which may indicate higher potential damage. |
| Categories | Focus on specific tactics, techniques, or attack components involved in incidents. |
| Entities | Filter by entity name or ID. |
| Data sensitivity | Show incidents where sensitive/valuable data may be involved (requires Microsoft Purview Information Protection). |
| Device group | Filter by defined device groups. |
| OS platform | Limit the incident queue view by operating system. |
| Classification | Filter incidents based on the classification of related alerts (true alerts, false alerts, or not set). |
| Automated Investigation state | Filter incidents by the status of the automated investigation. |
| Associated Threat | Enter threat information to bring up incidents with previous matching search criteria. |
Manage Incidents
There are many ways to manage incidents
- Edit the name of the incidents: Rename the incident to something more descriptive.
- Assign the incident to someone: The owner of the incident will be responsible for all the alerts within it.
- Set Status and Classification
- Status: Active or Resolved
- Classification: This is optional. You can pre-defined Microsoft categories like "True positive", "False positive", "Informational"). You can also add an optional description of it (or "determination"). i.e. malware, phising, etc.
- Add comments: Same idea as
git log - Add incident tag: Flag a group of incidents into one common characteristic. Think of it like a hash tag for Twitter.
Investigate Incidents
Describing severity comes with 4 colours:
- High (Red): Most commonly associated with Advanced Persistent Threats (APT). i.e. Credential theft tools activities, ransomware activities, security sensor affected, etc.
- Medium (Orange): Might be APT. It is akin to lower attack stages, abnormal registry keys changes, executation of suspicious files, etc.
- Low (Yellow): Alerts on threats associated with commonly known malware. It can also be anything that mimics admin/security tools tested by a user in the organization. i.e. clearing logs, running password dump utils, executing scripts with limited impact etc.
- Informational (Gray): It is not considered harmful to the network and informs the admins for potential security issues.
There are two types of software working together that scan for any threats:
- Microsoft Defender Antivirus (AV): Shows the absolute severity of the malware itself.
- Microsoft Defender for Endpoint (MDE): Shows the potential risk if the said malware is infected on an individual device.
Let's say a computer is not infected by a particular malware on the network, the threat will still show "Informational" because there was no actual damage to the computer.
Another factor is "Categories". "Categories" is one type of filter for an alert that follows the MITRE ATT&CK framework. It describes the objective and the technique done to the computer.
| Category | Description |
|---|---|
| Collection | Locating and collecting data for exfiltration. |
| Command and control | Connecting to attacker-controlled network infrastructure to relay data or receive commands. |
| Credential access | Obtaining valid credentials to extend control over devices and other resources in the network. |
| Defense evasion | Avoiding security controls (e.g., turning off security apps, deleting implants, running rootkits). |
| Discovery | Gathering information about important devices and resources (administrator computers, domain controllers, file servers). |
| Execution | Launching attacker tools and malicious code, including RATs and backdoors. |
| Exfiltration | Extracting data from the network to an external, attacker-controlled location. |
| Exploit | Exploit code and possible exploitation activity. |
| Initial access | Gaining entry to the target network (password-guessing, exploits, phishing emails). |
| Lateral movement | Moving between devices in the target network to reach critical resources or gain persistence. |
| Malware | Backdoors, trojans, and other types of malicious code. |
| Persistence | Creating autostart extensibility points (ASEPs) to remain active and survive system restarts. |
| Privilege escalation | Obtaining higher permission levels by running code in the context of a privileged process or account. |
| Ransomware | Malware that encrypts files and extorts payment to restore access. |
| Suspicious activity | Atypical activity that could be malware-related or part of an attack. |
| Unwanted software | Low-reputation apps or apps that impact productivity/user experience; detected as potentially unwanted applications (PUAs). |
Manage Automated Investigations
Alerts don't have to be resolved automatically. MED uses Automated Investigation and Remeditation (AIR) and are designed by examining alerts and take immediate action for any data breaches. It reduces alert volume and will help admins to have more time on sophisticated threats.
There are different types of automation:
-
Full: Remediate threats automatically entirely (it can be seen in Action Center on the History tab). A remediation action if full cannot be undone.
-
Semi: Requires approval for any remeditation. There are two types:
- Core folders remeditation: Anything under
\windows*or any other OS directories. - Non-temp folder remeditation: Includes any of these paths:
\users*\appdata\local\temp*\documents and settings*\local settings\temp*\documents and settings*\local settings\temporary*\windows\temp*\users*\downloads*\program files\\program files (x86)*\documents and settings*\users*
- Core folders remeditation: Anything under
-
No automated response: Other protective features will take place depending on how the antivirus and others are configured. This action is not recommended for enterprise/business usage.
Action Center
Incidents and Alerts --> Action Center
It is just like the Incidents page, but for pending or completed remeditation actions for devices, email and identities in one location by brining MDE and MOD together.
It has two items/tabs:
- Pending: Any investigations requiring attention by the security team in order to approve or reject.
- History:
- Result of an automated investigation
- Approved the security operations teamA
- Applied by Microsoft Defender Antivirus
- Commands that were run in Live Response sessions
If you wish to undo an action, you can apply the following ways:
- Isolate device
- Restrict code execution
- Quarantine a file
- Remove a registry key
- Stop a service
- Disable a driver
- Remove a scheduled task