Introduction to Directory Services
Categories: Computer Networking
Tags: Computer Networking
This article serves as a refresher for Directory Servers. It does not teach you how to set them up but aims to provide the information needed for people with some IT background.
Terminology
Directory server: A server that stores information about network resources and provides lookup services to map those resources to their addresses and attributes. It is used to organize and centralize user accounts, user groups, telephone numbers, and network shares.
Replication: A process carried out by directory servers to copy or synchronize data across other directory servers. It appears as a unified lump of data that helps maintain redundancy and lower latency.
Workgroup: It is an absract area made up of a collection of computers without a directory server.
- There is no central authority and each computer manages its own resources.
- Computers share information and resources through P2P (peer to peer).
Domain: An abstract area that share a common set of objectives.
- It includes computers, wires and everything within it.
- There is a central authority that provides all the configurations needed to function.
Organizational Unit (OU): It is a container object within an Active Directory (Microsoft's Directory server implementation) that holds user accounts, groups and computers. It is the "folders" of a domain.
Forest: It is a collection of trees and is the highest level of organization within an Active Directory.
Tree: It is a collection of domains within the Active Directory network.
Group Policy Object (GPO): It is a set of policies or preferences that are applied to a group of objects in a directory service.
Windows Registry: A low-level database made up of structured paths with keys and values that influence the behaviour of the Windows operating system.
All about Directory Services
Imagine there is a new, large corporation facility that is yet to be live and the staff is in urgent need to have their computer networks sorted out. We have to ensure the staff have access to their headquarters, organize data, and configure all the necessary settings for the local network.
Given this, it is crucial to centralize and streamline the management of all network resources and identities. This is precisely the role of Directory Services.
Understanding the Structure
What does "Directory Service" mean?
Directory Service (also known as just " Directory") refers to a software designed to manage and organize network resources. It uses a hierarchical structure to store information about various objects in the network and are stored on dedicated computers called directory servers.
Object: It is the smallest and most fundamental unit in a Directory Service. It represents a distinct entity, such as a user, computer, group, or resource, each with its own set of defined attributes.
It is no different from a reference book containing a person's name, phone number, street or email address etc.
What structure do Directory Services follow?
They are logically structured like trees in a forest. A company’s forest can contain multiple "trees", each made up of branches called "domains", with branches consisting of leaves referred to as "objects." As a result, each domain manages its own infrastructure.
Here is an illustration:
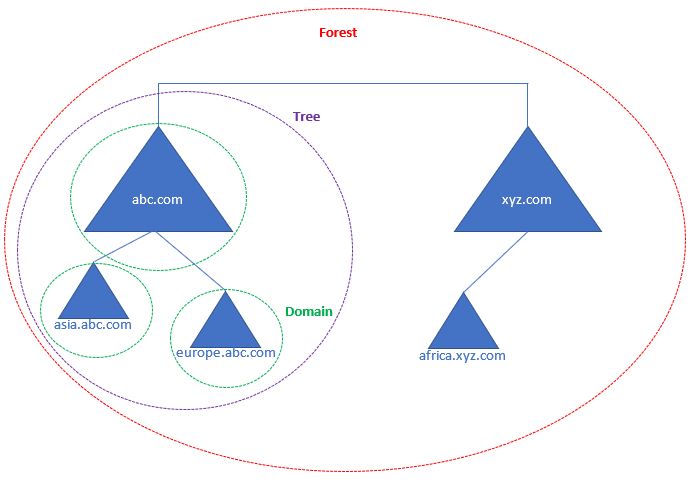
The forest is a collection of one or more trees (or just a single tree) organized under the same hierarchy.
The tree is a collection of one or more domains that share a contiguous namespace (in this example, we have abc.com and asia.abc.com).
The domain refers to an area within a network containing computers and user accounts. It serves as a boundary for security and administrative control.
Within each domain, directory servers centralize all network resources for authentication and authorization purposes. If we wish to further divide a company (or subsidiary) domain into separate "departments," we will need Organizational Units (OUs) and apply policies specific to each department.
For example, if we take the European branch of the company "ABC" (europe.abc.com), their departments can be organized into separate OUs like "Human Resources", "Finance", "Marketing" etc. This way, each department will need to behave differently or have authorized or unauthorized access of data.
User Authentication
What kind of user authentications are there for Directory Services?
In order to allow authenticating users within a domain, we need "Bind Operation". It is called "binding" because both the client and the server need to create a strong connection before data access.
There are three ways to achieve this:
-
Anonymous Bind: It is a connection request to a directory server without any credentials. It has no authentication and is prone to security risks (users without an account will be able to access the data).
-
Simple Bind: Requires a username and a password in plain text. It is recommended to set up an encryption for this (like SSL/TLS).
-
SASL (Simple Authentication and Security Layer) Bind: It is a framework that enables pluggable authentication protocols. It acts an intermediary layer forcing both the client and the server to negotiate (i.e. plain password/username, Kerberos ticket, etc.) while implementing a standard way to communicate.
Networking Protocols Involving Directory Servers
What are the protocols that interact with directory servers?
The most common protocol is "Lightweight directory access protocol" (LDAP). It is an extensible protocol that helps clients and servers query directory data.
There are multiple implementations of LDAP:
- Red Hat: Red Hat Directory Server
- IBM: IBM Security Verify Directory
- Microsoft: Active Directory or "AD"
- Oracle: Oracle Unified Directory
- OpenLDAP Project: Open LDAP (open source alternative)
In this article, we will only discuss Microsoft's Active Directory (AD) as it is the most common in a corporate setting.
Microsoft's Active Directory (AD)
"AD" is Microsoft's implementation of LDAP. Its most promiment component is Active Directory Domain Services (AD DS). AD DS is crucial to access networking objects.
Within AD DS, the core infrastructure is the Domain Controller (DC). In AD terminology, DC acts as the directory server that provides essential directory services and logic across the network.
We use two AD clients to manage AD DS.
- ADUC ("Active Directory Users and Computers")
- ADUC focuses more on users, groups, and computers.
- Older and more familiar to users and is a subset of ADAC (yes, a subset).
- ADAC ("Active Directory Administrator Center")
- ADAC is a more modern/comprehensive version of ADUC.
- ADAC provides extensive details and allows complete control.
We can also use Powershell cmdlets as well. It is the most versatile and powerful way to achieve the same results.
Note:
- AD clients are only available in Windows Pro and Enterprise editions. It is not possible to install in Windows Home or Standard Editions.
- AD clients need a server running Windows Server. You will need to deploy AD DS services in the server by following this guide (I highly recommend installing VMware Workstation Pro on and fire up Windows Server on it first).
When we interact with AD DS, we see that it has already organized its directory objects into different logical "containers". In AD lingo, a Container is a collection of objects that help us administer resources specific to their purpose within the Active Directory hierarchy.
If we wish to have separate departments for our infrastructure (i.e. "Marketing", "Human Resources", "IT" etc.), we create Organizational Units (OU) and have custom rules to facilitate our demands. These "rules" are referred to as "Group Policy" and are implemented as objects called Group Policy Objects (GPO).

So in bullet points, the hierarchy is as follows:
- Sites
-
Represents physical/geographic (non-logical) locations
-
One site can contain multiple domains
-
GPOs applied here affect all domains within the site
-
Domains
-
Logical boundary for authentication and policy enforcement
-
Identified by DNS name (e.g., corp.example.com)
-
Organizational Units (OUs)
-
Logical containers within a domain
-
Used to organize objects by department, function, etc.
-
GPOs can be applied here
-
Supports delegation of administrative control
-
Objects
- Users
- Computers
- Groups
- Printers
- Other resources
-
-
Containers
-
Default system containers (e.g., "Users", "Computers")
-
Cannot have GPOs applied
-
Used for basic organization of objects
- Objects
- Same as above: users, computers, etc.
- Objects
-
-
-
Important:
- Remember that OUs are containers, but not all containers are OUs. If the container has a GPO capability, then it is an OU.
- In AD lingo, a "domain" is a collection of containers and objects. They hold either built-in objects like "Computers" or "Users" or administrator-created OUs.
Understanding Group Policy Object (GPO)
GPO Introduction
GPOs are a set of policies or preferences applied to containers (OUs, Domains, or Sites) in Active Directory. They are used to enable or disable terminal access, USB support, max login attempt, wallpaper image, configure password reset, enforce complex password etc.
Policy: Another word for "rule". They are enforced settings that cannot be changed by users.
Preference: Configurable defaults that are applied once that can be changed by users. They are set back to their original configuration after every refresh or restart (i.e. setting a default printer or mapping a drive).
GPOs can contain either one or both types of these configurations:
- Computer Configuration: Applied as the computer is booting up once it is connected to the network. Examples include power management, firewall rules, software installations, secrurity settings etc.
- User Configurations: Applied at user sign in. Examples include Internet Explorer settings, folder redirection, moderate/limit Control Panel access etc.
In order to manage a GPO, we need to open Group Policy Management Console (GPMC) via gpmc.msc. To learn more about its usage, check out Microsoft's official documentation.
Here is an image showing the various types of security settings available under the "Windows Settings" subfolder:
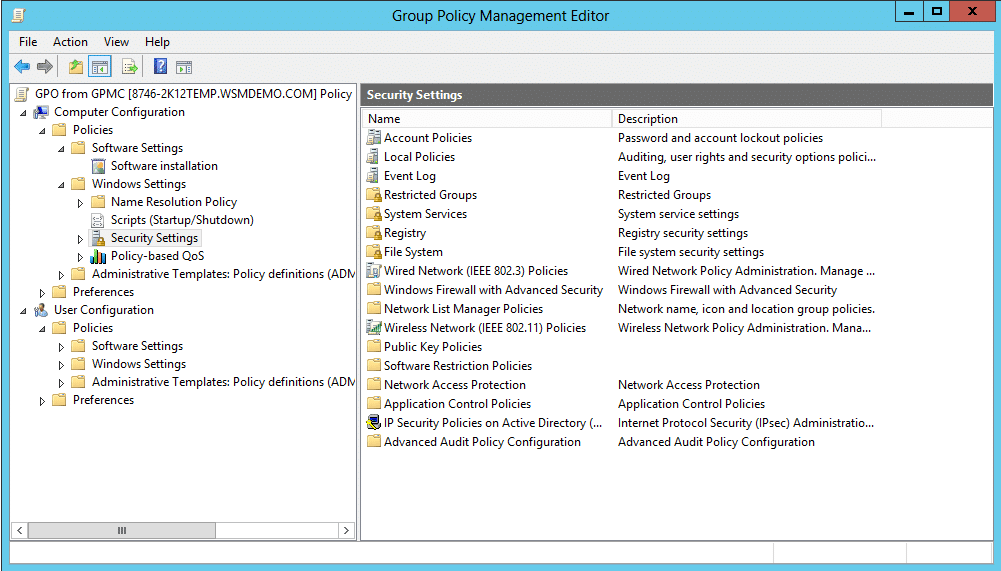
Almost all these policies are all represented as values in the Windows Registry. As soon they are linked on an OU, they will be written on the registry thereby affecting the Windows operating system functionality. We can see the list of connected OUs of a GPO under the Links section on the Scope tab in gpmc.msc.
Windows Registry: It is a hierarchical database that stores low-level settings and is usually solely used for administrative use. It is also an extremely sensitive part of the Windows operating system and is always referenced at run-time. In order to access it, we use regedit.exe.
For more info on Windows Registry, here is a general overview from Lifewire written by Tim Fisher and Microsoft's official documentation for advanced users.
To see what kind of policy settings are available, there are three references I recommend checking out (I highly recommend the first one):
-
Microsoft's official Group Policy Settings Reference (as of writing this, this is for Windows 11 24H2). If it is not available, here is a direct download.
-
GPS Search: It is a website to look up a a specific GPO (I still recommend checking out the spreadsheet).
Note:
- While checking for registry paths in regedit.exe, you might notice the shortcut HKLM for "HKEY_LOCAL_MACHINE" and HKCU for "HKEY_CURRENT_USER"
- Not all policy settings are directly mapped to the registry. Some settings rely on System APIs like user rights assignments) or password policies (stored in a security database like secedit.sdb).
- The exclamation mark (
!) in the registry path is not part of the actual registry syntax used inregedit.exe. It is there to separate the registry key path from the specific value name.So when you read this:
HKLM\Software\Policies\Microsoft\Windows Defender!DisableAntiSpywareIt means: “In the key
HKLM\Software\Policies\Microsoft\Windows Defender, set or check the value calledDisableAntiSpyware”
Here are some common policies to be aware of:
| Policy (Scope - Setting) | GPO Path | Registry Path |
|---|---|---|
| User - Disable Control Panel | User Configuration → Administrative Templates → Control Panel → "Prohibit access to Control Panel and PC Settings" → Select Enable | HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer!NoControlPanel(line 211 in the spreadsheet) |
| User - Disable Task Manager | User Configuration → Administrative Templates → System → Ctrl+Alt+Del Options → Remove Task Manager | HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System!DisableTaskMgr(Line 272 in the spreadsheet) |
| Computer - Turn off Windows Defender | Computer Configuration → Administrative Templates → Windows Components → Windows Defender Antivirus → Turn off Windows Defender Antivirus | HKLM\Software\Policies\Microsoft\Windows Defender!DisableAntiSpyware(Line 4201 in the spreadsheet) |
By right clicking and selecting 'Edit...' on any GPO, we will open Group Policy Management Editor (gpedit.msc). Through this, we are attempting to indirectly modify registry values of a group of computers, a specific computer, or an account etc.
Group Policy Inheritence
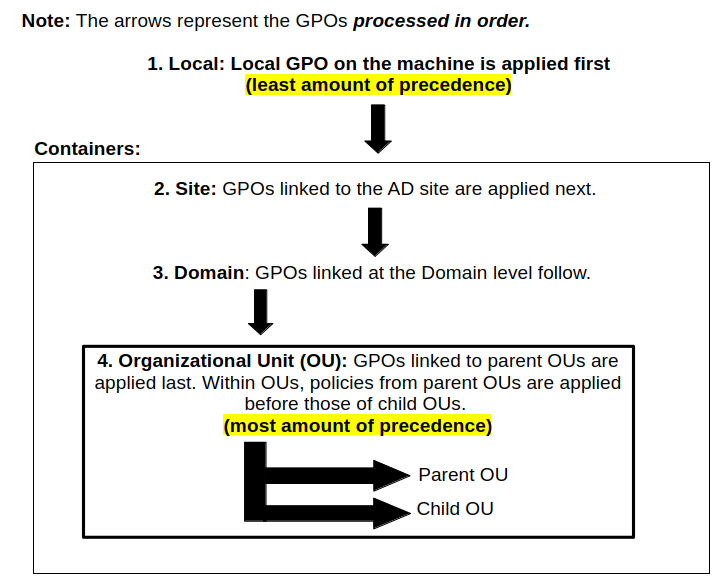
In case of GPO conflicts, they are applied by this order assuming there is no GPO blocking or enforcement applied (by clicking on the picture below, you will download the original file I used for this model (.odg for LibreOffice Draw):
In text:
- The Local GPO
- GPOs linked to Sites
- GPOs linked to Domains
- GPOs linked to OUs
- GPOs linked to parent OUs
- GPOs linked to child OUs
As each GPO is processed top to bottom as shown above, we might come across two conflicting GPOs with identical configurations. This is where precedence takes place.
Note: There is no link order to Local GPO because it is not a container. There are there to processes default configurations.
Understanding precedence:
Least precedence means it has a low priority. It makes the GPO more likely to be overidden by other GPOs.
Most precedence means is has a high priority. It makes the GPO less likely to be overidden by other GPOs.
Precedence is determined by two factors:
- The level of the container: i.e. Local, Site, Domain, OU. They are processed from top to bottom as illustrated above.
- The link order within that container: Applies only to Site, Domain, and OU levels. They are processed in a descending order (4,3,2,1..) but the precendence increases with every decrement:
- Link Order 3, 2, etc. are processed earlier --> lower precedence
- Link Order 1 is processed last --> highest precedence within that container
In a nutshell:
The highest number link order in the LEAST specific container is processed first... while the lowest number link order in the MOST specific container is processed last. The last one is applied in case of a conflict.
To see this in action, here is an excellent video made by Danny Moran. Note that he only touches on domain, parent OU, and child OU. He also touches on blocking and enforcing GPOs and how that affects ordering.
GPO Filtering
If we want to filter out a configuration within a specific set of objects, we have options in Group Policy Management Console:
- Security filtering: Determines which OUs (users and/or computer objects) are authorized to process GPO's configured settings. Here is Danny Moran explaining the intricacies of security filtering:
- WMI filtering: Narrows down operating systems, manufacturer name, hostname etc. at which GPO is applied. It is a much more expensive option because it relies on heavy calculations to verify operations infrastructure (hardware) and management data in the system.
- The successor to WMI is Windows Management Infrastructure (MI). It is backwards compatible to WMI.
- Here is an excellent WMI filtering cheat sheet and video made by Danny Moran:
Troubleshooting
Creating an RSoP Report:
Reluctant Set of Policy (RSoP): It is a report that includes policy information of a specified computer. It comes in handy for checking or testing a policy applied on a computer.
Note: RSoP is pronounced "R SAWP"
There are many ways to create an RSoP Report:
-
Group Policy Results Wizards:
- Open Group Policy Management Console (
gpmc.msc) - At the left panel tree, look for "Group Policy Results"
- Right click on it, then select "Group Policy Results Wizard"
- Select the target computer and user, then run the wizard to generate the report.
- Open Group Policy Management Console (
-
Command Prompt with
gpresultgpresult /rgpresult \h <filename>in an .html format
-
rsop.msc- Press Win + R, type rsop.msc, and press Enter.
- This opens a graphical console displaying the applied policies.
Windows Event Viewer
We can start Event Viewer by typing eventvwr.mscafter Win+R.
- Event Viewer: It is a Windows utility that helps track system problems and events related to items like applications, user logins, security, and systems. Any error messages or codes found in the logs can be investigated using the Microsoft Knowledge Base (support.microsoft.com). The main highlights include:
- System log: Records Windows OS events like hardware conflicts, driver load failures, service load failures, network issues, etc.
- Application log: Records application processes and utilities events/errors.
- Security log: Records system security audit information.
- Setup log: Records installation events and errors.
Here is an official video presentation by Microsoft exploring Event Viewer's overall functionality.
Importants Commands to Remember:
gpresult: Displays an RSoP report for a computer and user account. It also helps ascertain which configuration settings have been applied and which settings were overridden.
Some popular switches include:
- /s host: Displays the RSoP values of a remote computer.
- /u user-account: Displays the RSoP values of an end-user.
- /p password: Displays the RSoP values of an end-user password policy.
- /r: Displays the RSoP summary of applied GPOs.
- /z: Turns on verbose mode to display details of the RSoP applied settings.
gpedit: a.k.a Local Group Policy Editor. It is a robust tool for changing registry settings related to the Control Panel, settings, user profiles, system configurations, third-party software, etc.
gpupdate: In case if you would like to immediately see an updated GPO, you can force it by using the /force switch. Depending on the policy setting, if it requires users to log off or reboot, the switches /logoff or /boot can be added to the command.
References
- https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/get-started/virtual-dc/active-directory-domain-services-overview
- https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/plan/understanding-the-active-directory-logical-model
- https://delinea.com/what-is/active-directory
- https://www.amazon.ca/Mastering-Active-Directory-Dishan-Francis/dp/1787289354
- https://en.wikipedia.org/wiki/Active_Directory
- https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/group-policy/group-policy-overview
- https://www.openldap.org/doc/admin26/intro.html